Ransomware Becomes Top Cyber Threat
It is easy for organizations to become numb to the threat of ransomware. Many choose to believe that their business is either too small to be a likely target or that your existing cybersecurity measures provide adequate protection. Unfortunately, this optimism has led to the peril of many organizations. SonicWall recently reported there have been 181.5 million ransomware attacks during the first six months of 2018, which marks a 229 percent increase over this same time frame in 2017. Encrypted threats are up 275 percent over last year.
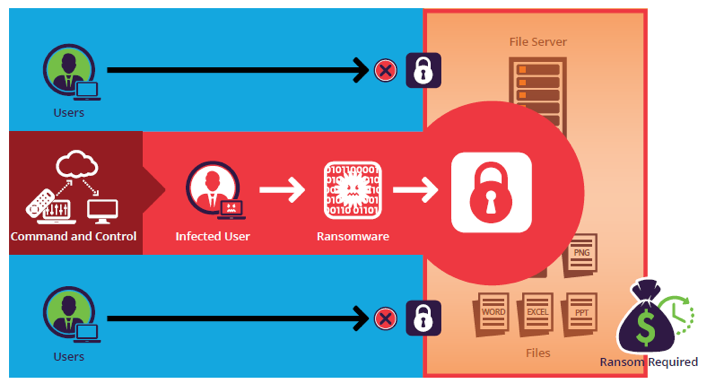
There are a few factors contributing to ransomware becoming the primary cyber security threat out there.
- Removes issue of finding a buyer. The key for cybercriminals is finding a buyer that is willing to pay. When it comes to selling data on the dark web, searching for a buyer is tricky and comes with many risks. Selling something directly to the person you stole it from improves the odds of getting paid quickly and quietly.
- NSA Breach. In 2017, Shadow Brokers compromised government security defenses and delivered to the world the tools the NSA had been using to break into computers of its adversaries. These tools are now being used by hackers from North Korea to Russia to target businesses and civilians. The WannaCry attack was created using these tools, as was the Petya attack which shut down millions of computers across the globe with demands for payments to restore access.
- Cryptocurrency. Gone are the days of money laundering, in its place is cryptocurrency. Anyone can sign up for a cryptocurrency wallet in a matter of minutes and most cyber criminals even provide their victims with instructions on how to do so. With cryptocurrency, neither the wallet nor the resulting transactions can be easily connected to any real-world identities.
- Ransomware-as-a-Service. Developing malware no longer requires coding skills and knowledge of operating systems, networking and hardware. Ransomware-as-a-Service can now be purchased cheaply on the dark web and is very easy to use. Some vendors even offer customer support for buyers of their malware. Cybercriminals who want customized ransomware can hire black-hat coders for its development.
Cybersecurity is a complex problem that requires multiple layers of defense. Organizations need to implement endpoint technologies such as antivirus, anti-malware software and firewalls to keep intruders out. You must also acquire the necessary resources to keep up with frequent software, data backups, equipment security updates, as well as providing security training for staff. It is also necessary to develop and implement security best practices for your business. 2W Tech is a full service IT Consulting firm that has IT Consultants on staff that specialize in Security solutions. Give us a call today to ensure you don’t become the next victim of Ransomware.
Read More:
SharePoint Keeps Businesses Functioning Across Platforms
Why is Artificial Intelligence Important?
7 Steps to a Holistic Security Strategy
Interested in reading this article? Click the button below to download this asset.
Download “7 Steps to a Holistic Security Strategy” Now
7 Steps to a Holistic Security Strategy
Please complete the form to download the file.