How Your Business Can Benefit From Axcient Fusion
2W Tech worked with a few clients over the last month that got infected by CryptoLocker. The good news, is that each of these clients chose Axcient Fusion for their disaster recovery product. This ransomware typically propagated as an attachment to a seemingly innocuous e-mail message, which appears to have been sent by a legitimate company. While security software is designed to detect such threats, it might not detect CryptoLocker at all, or only after encryption is underway or complete. 2W Tech was alerted of the attacks through the Axcient remote monitoring software and then reached out to the clients. This strand of malware caused a server crash and complete operating system corruption.
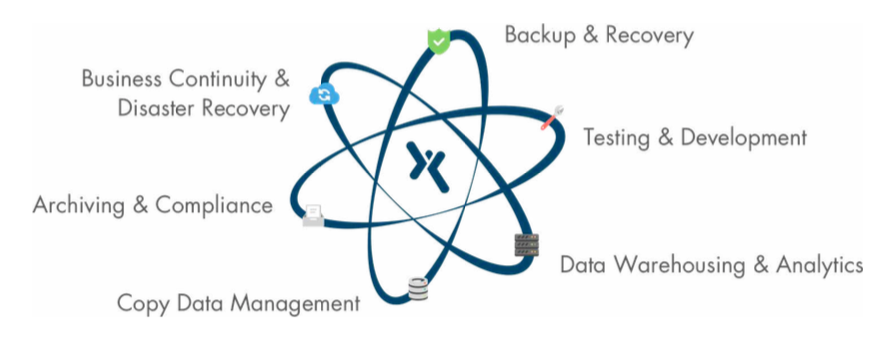
While the steps 2W Tech took for these clients varied, one factor remained the same. Axcient Fusion may have saved all of these organizations from going out of business. Not one organization had downtime of more than 2 hours, saving them time and money. Axcient Fusion allow for the quick recovery of of the clients environment, while still letting them operate. With most other disaster recovery solutions, you can not do that. You must wait to rebuild the server and backup data before you can continue to operate.
Choosing the right disaster recovery solution can be a difficult task due to the cost and complexity. Given the unpredictability and large amount of threats businesses are faced with, it is important that you chose the right solution. Axcient Fusion allows you to reduce your costs and complexity, while increasing your IT resilience. Axcient Fusion delivers the critical capabilities that will give your business peace of mind in knowing you can recover quickly from anything thrown your way. To learn more about the Fusion product, give 2W Tech a call today. We have hands-on experience with clients using this product and can share some of these experiences with you to help you decide if this solution is the best fit for your business.
Read More:
Azure Resources Provide Safety For Cloud Computing
Smart Manufacturing is the Future
7 Steps to a Holistic Security Strategy
Interested in reading this article? Click the button below to download this asset.
Download “7 Steps to a Holistic Security Strategy” Now
7 Steps to a Holistic Security Strategy
Please complete the form to download the file.