WannaCry Ransomware: What You Need to Know
Over the weekend, we witnessed a new global cyberattack known as WannaCry Ransomware. This malicious software has locked thousands of computers in more than 150 countries. The attack has hit more than 300,000 computers so far. In the U.S, the reported list of victims is very small however, it is still relatively early in this attack. WannaCry is a type of malware that is classified as ransomware. It encrypts essential files on your Windows device and requires that you pay a $300 ransom to unlock those files. This WannaCry ransomware primarily focuses on organizational or business networks by leveraging a flaw within the way organizations’ networks allow devices to talk to each other. It is not meant to attack consumers or go after personal data.
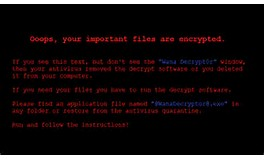
Here are some steps your organization needs to take to help stop the spread of ransomware:
- Keep your security software updated. If you are using a cloud version, your updates are automatic. If you are not, make sure you are running the latest version of the software. As new variants of software arise, security software makes adjustments to keep you protected but only if you have the latest version.
- Apply any Microsoft Windows security patches that Microsoft has sent you. If you are using an older version of Microsoft’s operating systems, such as Windows XP or Windows 8, check to see if any emergency patches are available to you.
- Do not click on anything that seems suspicious. This malware was distributed by phishing emails. You should only click on emails that you are sure came from a trusted source and look like a legit email.
- Backup all your devices, including pcs, tablets, and any other devices connected to your network. If you use a OneDrive, be sure that you have a backup solution for that as well. Regularly backing up your devices helps you recover your information should your computer become infected with ransomware.
What separates WannaCry Ransomware from other attacks we’ve seen is that the tactic itself has been used before and it pretty common for a ransomware strand, exploiting a flaw in several versions of Microsoft’s Windows operating system that was well-known and well-publicized. A patch Microsoft issued in March to fix the issue could have taken businesses and organizations just a day or two to test and install. It has also been reported that many Cybersecurity Specialist warned of this attack in the weeks leading up, but many organizations and security solution providers didn’t take the steps to protect themselves and their clients.
Bottom line, this attack could have been prevented if organizations ensured they were running the most current version of security software and if they ensured that they had no gaps in their security coverage. You can’t control the risks users expose you to, but you can control the protection you are willing to offer your organization. You should ensure that you are working with a IT Consultant that specializes is security solutions, as well as offers cloud delivery. Why risk gaps in coverage because your software upgrade was a day or 2 behind. Cloud ensures the most recent, available version is automatically delivered to your organization. 2W Tech has IT Consultants on staff that specialize in security solutions. 2W also offers total security protection solutions, everything from our Failover device, OneDrive protection, all the way to a full solution that covers all areas of your network and data. Call us today and ensure you never go unprotected again.
Read More:
Three Phases of Ransomware
Why You Need a Cloud Strategy
Best Practices in Disaster Recovery Whitepaper
Enjoyed reading this article? Click the button below to download this asset.
Download “Best Practices in Disaster Recovery” Now
Best Practices in Disaster Recovery Whitepaper
Please complete the form to download the file.