What is a Vulnerability Assessment?
A vulnerability assessment is the process of defining, identifying, classifying and prioritizing vulnerabilities in computer systems, applications and network infrastructures. This assessment provides the organization doing the assessment with the necessary knowledge, awareness and risk background to understand the threats to its environment and react appropriately. Vulnerability assessments are designed to yield a prioritized list of a system’s vulnerabilities for various kinds of threats. Organizations that use these assessments are aware of security risks and understand they need help identifying and prioritizing potential issues.
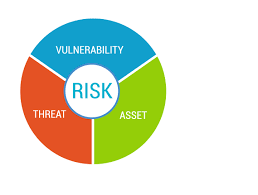
Vulnerability assessments differ for all the areas of an organization’s technology center. IT systems like a website with databases, may require an assessment of its vulnerability to hackers and other forms of cyberattacks. On the other hand, a data center may require an assessment of both physical and virtual vulnerabilities because it requires security for its physical facility and cyber presence. The main goal of a vulnerability assessment, regardless of for what area, is to verify that security initiatives are effective. Whether your organization develops applications or uses third-party applications, conducting a vulnerability assessment at least annually, or after significant changes to the applications or application environments are implemented, is critical to ensure the highest level of security for your organization. Contact 2W Tech today to get started on your vulnerability assessment.
Read More:
View Your Business at a Glance by 2W Tech
Economics of Serverless Cloud Computing
Interested in reading this article? Click the button below to download this asset.
Download “Economics of Serverless Cloud Computing” Now
Economics of Serverless Cloud Computing
Please complete the form to download the file.